Web-fu Is a web hacking tool focused on discovering and exploiting web vulnerabilitites.
BROWSER INTEGRATION
This tool has many advantages, as a browser-embedded webhacking tool, is very useful for scanning browser-authenticated applications, if browser can authenticate and access to the web application, the tool also can. Note that some other tools do not support neither certificate authentication nor web vpn accesses.
The integration with chrome, provides a more comfortable and agile way of web-hacking, and you have all the application data loaded on the hacking tool, you don't need to copy the url, cookies, etc. to the tool, just right click and hack.
The browser rendering engine is also used in this tool, to draw the html of the responses.
FALSES POSITIVES
When I coded this tool, I was obsessed with false positives, which is the main problem in all detection tools. I have implemented a gauss algorithm, to reduce the faslse positives automatically which works very very well, and save a lot of time to the pentester.
VIDEO
Here is a video, with some of the web-fu functionalitites:
VISUAL FEATURES
This tool has a visual crawler. Normal crawlers doesn't parse the ajvascript, this tool does. The visual crawler loads each link of the web site, rendering the html and executing all the javascript as a normal load, then the links are processed from he DOM and clicked.
A visual form cracker, is also available, althow is experimental and only works on some kind of forms.
SCANNING FEATURES
The web-fu's portscanner, has a database of a common web ports, like 80,81,8080 and so on.
The cracker module, can bruteforce web directories to find new attack vectors, and can fuzz get and post parameters for discovering vulns, and also crack passwords. There are 9 preloaded wordlists, and you can also load a custom wordlist. Prefilters, falsepositive reductor and render will be helpful. The scanners support SSL, if the website can be loaded in the chrome, can be scanned by web-fu.
ENCODERS & DECODERS
The supported encoders and decoders are: base64, urlescape and urlencode
OTHER FEATURES
A web notepad is available, saving the information on the browser localStorage, there is one notepad per site. A cookie editor is also very useful for pentesting. The inteceptor, is like a web proxy but from the inside of the browser, you can intercept a request There is also a session locker and a exploit web search.
CHROME STORE
Here is the link to the chrome store, the prize is about one euro, very cheap if you compare with other scanners: Web-Fu on Chrome Store
With webfu, you will do the best web site pentest and vulnerability assessment.
Continue reading
Sunday, 26 April 2020
Saturday, 25 April 2020
Ethical Hacking Platform For Penetration Testing | How To Hack The Invite Code: Join Hack The Box (HTB)
Hack The Box
Hack The Box (HTB) is a free platform available to ethical hackers to do a penetration testing for ethical hacking projects. It consist of different type of challenges that are updated constantly. Some of the challenges related to the real world scenarios and rest of the challenges related to learning towards a CTF style of challenges.Before joining to HTB, there is a simple task for you to prove your skills after that you'll able to create an account, and then you'll be able to access to your HTB Lab, where several challenges await for you to hack them. That's the beginning step for all of us to joining this. If you got success while hacking then you'll get points.
Task For Joining The HTB
Before joining the HTB, there is a task to hack invite code and paste that code in the code box for further registration to your account. You can complete a simple challenge to prove your skills, if you don't hack that then here is a short video below this content about hacking the invite code. Watch the video and hack the code!
In this Video you'll learn about How to join Hack the box (HTB) in Kali Linux and other Linux Distributions.
More articles
Hacking PayPal's Express Checkout
Do you know what is happening in the background when you buy something in an online shop using PayPal?
In this post we will tackle the following problems:
- How can PayPal's API be tested?
- How does PayPal's Express Checkout work? You can find the detailed report here.
- How can we debit more money than authorized?
How PayPal's API can be tested?
PayPal's Sandbox API
PayPal offers a feature called PayPal Sandbox Accounts, which mimics the production API. The basic idea is that a normal user/shop can test the API and make transactions without actually transferring money. This is the perfect tool for developers to test their API integration.Access to all messages
The next question is how to get access to all messages. All browser-related messages can be inspected, intercepted, and modified via BurpSuite. The main problem here is how to get access to the server-to-server exchanged messages: the messages exchanged between PayPal and a shop. In order to solve this problem, we deployed our own shop. For this purpose we used Magento, which already has a PayPal integration.Once we have our own controlled shop, we can enforce Magento to send all request through a proxy.
In the following picture you can see our setup.
 |
| Test suite for analyzing PayPal's API [1] |
In order to capture the traffic between our Magento hhop and PayPal we proceeded as follows:
- We configured Magento to use a proxy running on localhost:8081.
- We connected the proxy port on the virtual machine with our local machine via SSH remote port forwarding by issuing the following command
- We configured BurpSuite running on our local machine to listen on Port 8081 for incoming requests.
Please note that we uses our own, custom Magento shop in order to be able to test Paypal's API.
PayPal's Express Checkout
An overview of the checkout procedure is depicted in the following: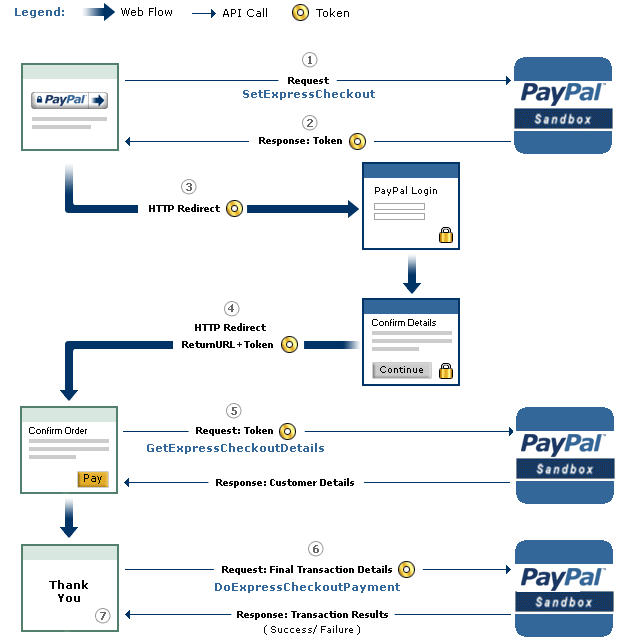 | ||||
| PayPal's Express Checkout [2] |
Step 1: Magento tells the PayPal API where to redirect the user after authorizing the transaction via the parameter RETURNURL and requests a token for this transaction.
Step 2: The PayPal API provides Magento with the token.
Step 3: Magento redirects the user to PayPal's website. The redirect contains the token from the previous step.
Step 4: The user authorizes the transaction. As a result, he will be redirected back to Magento (RETURNURL) with the token.
Step 5: Magento issues a request to the PayPal API to get the transaction details.
Step 6: Magento signals the PayPal API to execute the transaction.
Step 7: Magento serves the success page.
A more detailed view of the protocol and all parameters is shown on page 16 in the full version. We will concentrate only on step 6 and the parameters relevant for the attack.
The Attack
The goal of the attack is to let a shop (in our case Magento) debit more money than authorized by the PayPal user. The core of the attack is Step 6 -- DoExpressCheckoutPayment. Let's get a deeper look at this message: |
| Magento can raise the authorized amount and debit more money from the user's account |
- The shop sends the token, which was issued in the first step of the protocol and identifies uniquely the transaction through all steps.
- The PayerID referring to the user that authorized the payment.
- The AMT defining the amount, which will be transferred.
- The API Credentials authenticating Magento on PayPal.
- The Version pointing to the release number of the API.
As one can imagine, the core problem we found was the change of the AMT parameter. This value can be freely chosen by the shop, despite the fact that the user has authorized a different amount.
We tested only the SandBox API, but refused to test the production API in order to avoid problems. We promptly contacted PayPal's security team and described the problem hoping that PayPal can and will test the production API against the attack.
The response of PayPal can be summarized as follows:
- We don't get any BugBounty since we only tested the Sanbox API. (Fair enough)
- In the Production API PayPal this flexibility is a wanted feature. Thus, PayPal allows a merchant to charge for shipping and/or other expenses different amounts. Any malicious behavior can be detected by PayPal. In case of fraudulent charges the consumer are protected by the Buyer Protection policy.
Authors of this Post
Daniel HirschbergerVladislav Mladenov
Christian Mainka (@CheariX)
[1] BurpSuite Logo
[2] PayPal Express Checkout
Related word
How To Hack Facebook By Social Engineering Attack
This video is specially for educational purpose only. I'm not responsible for your any illegal activity. Thanks!
Social Engineering Attack
Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details (and money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. The purpose of this video tutorial is to show you How hackers hacked any thing by Social Engineering Attack.Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The information is then used to access important accounts and can result in identity theft and financial loss.
Kali Linux has many tools for doing social engineering attacks. Setoolkit is the most powerful tool in Kali Linux to do a social engineering attacks over the same and different networks.
Social Engineering over the same network requires the local IP address of your system just like this one 192.168.1.2. Now how you can get your local IP address from your system. To find local IP address just open up your terminal in Linux distribution:
Type: ifconfig wlan0 (if you are using WiFi)
Type: ifconfig eth0 (if you are using eth0)
Type: ifconfig (It display all information about your network)
Now you've another thing to do is that you just have to clone a web page you wanna clone like Facebook, g-mail, twitter etc. Similarly, If you wanna clone a facebook page so for this you just have to type www.facebook.com over your system's terminal for cloning a login page for Social Engineering attack.Still If you don't know how to do that so don't be worry, I did all the process practically in the below just go down and watch it!
How hackers do Social Engineering Attacks. In this video you'll see How to hack Facebook by Phishing attack.
Read more
Blockchain Exploitation Labs - Part 1 Smart Contract Re-Entrancy
Why/What Blockchain Exploitation?
In this blog series we will analyze blockchain vulnerabilities and exploit them ourselves in various lab and development environments. If you would like to stay up to date on new posts follow and subscribe to the following:Twitter: @ficti0n
Youtube: https://www.youtube.com/c/ConsoleCowboys
URL: http://cclabs.io
http://consolecowboys.com
As of late I have been un-naturally obsessed with blockchains and crypto currency. With that obsession comes the normal curiosity of "How do I hack this and steal all the monies?"
However, as usual I could not find any actual walk thorough or solid examples of actually exploiting real code live. Just theory and half way explained examples.
URL: http://cclabs.io
http://consolecowboys.com
As of late I have been un-naturally obsessed with blockchains and crypto currency. With that obsession comes the normal curiosity of "How do I hack this and steal all the monies?"
However, as usual I could not find any actual walk thorough or solid examples of actually exploiting real code live. Just theory and half way explained examples.
That question with labs is exactly what we are going to cover in this series, starting with the topic title above of Re-Entrancy attacks which allow an attacker to siphon out all of the money held within a smart contract, far beyond that of their own contribution to the contract.
This will be a lab based series and I will show you how to use demo the code within various test environments and local environments in order to perform and re-create each attacks for yourself.
Note: As usual this is live ongoing research and info will be released as it is coded and exploited.
Note: As usual this is live ongoing research and info will be released as it is coded and exploited.
If you are bored of reading already and just want to watch videos for this info or are only here for the demos and labs check out the first set of videos in the series at the link below and skip to the relevant parts for you, otherwise lets get into it:
Background Info:
This is a bit of a harder topic to write about considering most of my audience are hackers not Ethereum developers or blockchain architects. So you may not know what a smart contract is nor how it is situated within the blockchain development model. So I am going to cover a little bit of context to help with understanding. I will cover the bare minimum needed as an attacker.
A Standard Application Model:
- In client server we generally have the following:
- Front End - what the user sees (HTML Etc)
- Server Side - code that handles business logic
- Back End - Your database for example MySQL
A Decentralized Application Model:
Now with a Decentralized applications (DAPP) on the blockchain you have similar front end server side technology however
- Smart contracts are your access into the blockchain.
- Your smart contract is kind of like an API
- Essentially DAPPs are Ethereum enabled applications using smart contracts as an API to the blockchain data ledger
- DAPPs can be banking applications, wallets, video games etc.
A blockchain is a trust-less peer to peer decentralized database or ledger
The back-end is distributed across thousands of nodes in its entirety on each node. Meaning every single node has a Full "database" of information called a ledger. The second difference is that this ledger is immutable, meaning once data goes in, data cannot be changed. This will come into play later in this discussion about smart contracts.
Consensus:
The blockchain of these decentralized ledgers is synchronized by a consensus mechanism you may be familiar with called "mining" or more accurately, proof of work or optionally Proof of stake.
Proof of stake is simply staking large sums of coins which are at risk of loss if one were to perform a malicious action while helping to perform consensus of data.
Proof of stake is simply staking large sums of coins which are at risk of loss if one were to perform a malicious action while helping to perform consensus of data.
Much like proof of stake, proof of work(mining) validates hashing calculations to come to a consensus but instead of loss of coins there is a loss of energy, which costs money, without reward if malicious actions were to take place.
Each block contains transactions from the transaction pool combined with a nonce that meets the difficulty requirements. Once a block is found and accepted it places them on the blockchain in which more then half of the network must reach a consensus on.
The point is that no central authority controls the nodes or can shut them down. Instead there is consensus from all nodes using either proof of work or proof of stake. They are spread across the whole world leaving a single centralized jurisdiction as an impossibility.
Things to Note:
First Note: Immutability
- So, the thing to note is that our smart contracts are located on the blockchain
- And the blockchain is immutable
- This means an Agile development model is not going to work once a contract is deployed.
- This means that updates to contracts is next to impossible
- All you can really do is createa kill-switch or fail safe functions to disable and execute some actions if something goes wrong before going permanently dormant.
- If you don't include a kill switch the contract is open and available and you can't remove it
Second Note: Code Is Open Source
- Smart Contracts are generally open source
- Which means people like ourselves are manually bug hunting smart contracts and running static analysis tools against smart contract code looking for bugs.
When issues are found the only course of action is:
- Kill the current contract which stays on the blockchain
- Then deploy a whole new version.
- If there is no killSwitch the contract will be available forever.
Now I know what you're thinking, these things are ripe for exploitation.
And you would be correct based on the 3rd note
Third Note: Security in the development process is lacking
- Many contracts and projects do not even think about and SDLC.
- They rarely add penetration testing and vulnerability testing in the development stages if at all
- At best there is a bug bounty before the release of their main-nets
- Which usually get hacked to hell and delayed because of it.
- Things are getting better but they are still behind the curve, as the technology is new and blockchain mostly developers and marketers. Not hackers or security testers.
Forth Note: Potential Data Exposure via Future Broken Crypto
- If sensitive data is placed on the blockchain it is there forever
- Which means that if a cryptographic algorithm is broken anything which is encrypted with that algorithm is now accessible
- We all know that algorithms are eventually broken!
- So its always advisable to keep sensitive data hashed for integrity on the blockchain but not actually stored on the blockchain directly
Exploitation of Re-Entrancy Vulnerabilities:
With a bit of the background out of the way let's get into the first attack in this series.
Re-Entrancy attacks allow an attacker to create a re-cursive loop within a contract by having the contract call the target function rather than a single request from a user. Instead the request comes from the attackers contract which does not let the target contracts execution complete until the tasks intended by the attacker are complete. Usually this task will be draining the money out of the contract until all of the money for every user is in the attackers account.
Example Scenario:
Let's say that you are using a bank and you have deposited 100 dollars into your bank account. Now when you withdraw your money from your bank account the bank account first sends you 100 dollars before updating your account balance.
Well what if when you received your 100 dollars, it was sent to malicious code that called the withdraw function again not letting the initial target deduct your balance ?
With this scenario you could then request 100 dollars, then request 100 again and you now have 200 dollars sent to you from the bank. But 50% of that money is not yours. It's from the whole collection of money that the bank is tasked to maintain for its accounts.
Ok that's pretty cool, but what if that was in a re-cursive loop that did not BREAK until all accounts at the bank were empty?
That is Re-Entrancy in a nutshell. So let's look at some code.
Example Target Code:
function withdraw(uint withdrawAmount) public returns (uint) {
1. require(withdrawAmount <= balances[msg.sender]);
2. require(msg.sender.call.value(withdrawAmount)());
3. balances[msg.sender] -= withdrawAmount;
4. return balances[msg.sender];
}
Line 1: Checks that you are only withdrawing the amount you have in your account or sends back an error.
Line 2: Sends your requested amount to the address the requested that withdrawal.
Line 3: Deducts the amount you withdrew from your account from your total balance.
Line 4. Simply returns your current balance.
Ok this all seems logical.. however the issue is in Line 2 - Line 3. The balance is being sent back to you before the balance is deducted. So if you were to call this from a piece of code which just accepts anything which is sent to it, but then re-calls the withdraw function you have a problem as it never gets to Line 3 which deducts the balance from your total. This means that Line 1 will always have enough money to keep withdrawing.
Let's take a look at how we would do that:
Example Attacking Code:
function attack() public payable {
1. bankAddress.withdraw(amount);
}
2. function () public payable {
3. if (address(bankAddress).balance >= amount) {
4. bankAddress.withdraw(amount);
}
}
Line 1: This function is calling the banks withdraw function with an amount less than the total in your account
Line 2: This second function is something called a fallback function. This function is used to accept payments that come into the contract when no function is specified. You will notice this function does not have a name but is set to payable.
Line 3: This line is checking that the target accounts balance is greater than the amount being withdrawn.
Line 4: Then again calling the withdraw function to continue the loop which will in turn be sent back to the fallback function and repeat lines over and over until the target contracts balance is less than the amount being requested.
Review the diagram above which shows the code paths between the target and attacking code. During this whole process the first code example from the withdraw function is only ever getting to lines 1-2 until the bank is drained of money. It never actually deducts your requested amount until the end when the full contract balance is lower then your withdraw amount. At this point it's too late and there is no money left in the contract.
Setting up a Lab Environment and coding your Attack:
Hopefully that all made sense. If you watch the videos associated with this blog you will see it all in action. We will now analyze code of a simple smart contract banking application. We will interface with this contract via our own smart contract we code manually and turn into an exploit to take advantage of the vulnerability.
Download the target code from the following link:
Then lets open up an online ethereum development platform at the following link where we will begin analyzing and exploiting smart contracts in real time in the video below:
Coding your Exploit and Interfacing with a Contract Programmatically:
The rest of this blog will continue in the video below where we will manually code an interface to a full smart contract and write an exploit to take advantage of a Re-Entrency Vulnerability:
Conclusion:
WHAT IS ETHICAL HACKING
Ethical hacking is identifying weakness in computer system and/or computer networks and coming with countermeasures that protect the weakness.
Ethical hackers must abide by the following rules-
1-Get written permission from the owner of the computer system and/or computer network before hacking.
2-Protect the privacy of the organisation been hacked etc.
Ethical Hacking and Ethical Hacker are terms used to describe hacking performed by a company or individual to help identity potential threats on a computer or network.
Ethical hackers must abide by the following rules-
1-Get written permission from the owner of the computer system and/or computer network before hacking.
2-Protect the privacy of the organisation been hacked etc.
Ethical Hacking and Ethical Hacker are terms used to describe hacking performed by a company or individual to help identity potential threats on a computer or network.
An Ethical Hacker attempts to byepass system security and search for any weak point that could be exploited by Malicious Hackers.
More info
Friday, 24 April 2020
HOW TO CAPTURE SCREENSHOT IN KALI LINUX? – KALI LINUX TUTORIAL
Kali Linux has been the most advanced penetration testing machine introduced yet. It has the most valuable tools used for every sort of hacking. To take advantage of Kali Linux hacking tools, you have to switch your OS to Kali Linux. You can either install Kali Linux as your default OS or just install as a virtual machine within the same OS. You can learn more about how to install Kali Linux Virtualbox. Today in this tutorial, I am just going to share a very simple Kali Linux tutorial on how to capture screenshot in Kali Linux. It's very simple and newbie friendly.
SO, HOW TO CAPTURE SCREENSHOT IN KALI LINUX? – KALI LINUX TUTORIAL
There are two ways to capture a screenshot in Kali Linux. One is the ultimate easy one and the second one is a bit complex but it's also not so complicated. So, don't worry about anything.
INSTRUCTIONS TO FOLLOW
- In a first way, you can take a screenshot in a similar way as you take in Windows OS by simply clicking the PrntScr button on the keyboard. As you hit that button, a screenshot will be saved in the Pictures folder of your Kali Linux. The major problem with it, it only captures the full screen. We have no control over it to capture a specific window or region.
- The second way is to take a screenshot using the command. For that, open up a terminal in the Kali Linux and type apt-get install ImageMagick.
- Once the command is completed and ImageMagick is installed. We have two options to take a screenshot with it. One is to capture full screen and second is to capture a specific window.
- To capture full screen, type import -window root Pictures/AnyNameOfTheImage.png in the terminal. It will take a full screenshot and will save it to the Pictures directory by the name you specify. Make sure to type .png at the end of the file name.
- To take a screenshot of a specific window or region, type import Pictures/AnyNameOfTheImage.png in the terminal and hit Enter, it will turn the cursor to a selection tool. You just click the mouse button and select the area you want to capture. As you will leave the mouse key, screenshot will be saved in the Pictures folder.
That's all how you can capture screenshot in Kali Linux. This is a very simple and beginner-friendly Kali Linux tutorial to help out all the newbies how they can use this features in need. Hope it will be useful for you.
More articles
Thursday, 23 April 2020
Potao Express Samples
http://www.welivesecurity.com/2015/07/30/operation-potao-express/
http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
TL; DR
More informationhttp://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
TL; DR
2011- July 2015
- Aka Sapotao and node69
- Group - Sandworm / Quedagh APT
- Vectors - USB, exe as doc, xls
- Victims - RU, BY, AM, GE
- Victims - MMM group, UA gov
- truecryptrussia.ru has been serving modified versions of the encryption software (Win32/FakeTC) that included a backdoor to selected targets.
- Win32/FakeTC - data theft from encrypted drives
- The Potao main DLL only takes care of its core functionality; the actual spying functions are implemented in the form of downloadable modules. The plugins are downloaded each time the malware starts, since they aren't stored on the hard drive.
- 1st Full Plugin and its export function is called Plug. Full plugins run continuously until the infected system is restarted
- 2nd Light Plugin with an export function Scan. Light plugins terminate immediately after returning a buffer with the information they harvested off the victim's machine.
- Some of the plugins were signed with a certificate issued to "Grandtorg":
- Traffic
- Strong encryption. The data sent is encapsulated using the XML-RPC protocol.
- MethodName value 10a7d030-1a61-11e3-beea-001c42e2a08b is always present in Potao traffic.
- After receiving the request the C&C server generates an RSA-2048 public key and signs this generated key with another, static RSA-2048 private key .
- In 2nd stage the malware generates a symmetric AES-256 key. This AES session key is encrypted with the newly received RSA-2048 public key and sent to the C&C server.
- The actual data exchange after the key exchange is then encrypted using symmetric cryptography, which is faster, with the AES-256 key
- The Potao malware sends an encrypted request to the server with computer ID, campaign ID, OS version, version of malware, computer name, current privileges, OS architecture (64 or 32bits) and also the name of the current process.
- Potao USB - uses social engineering, exe in the root disguised as drive icon
- Potao Anti RE - uses the MurmurHash2 algorithm for computing the hashes of the API function names.
- Potao Anti RE - encryption of strings
- Russian TrueCrypt Win32/FakeTC - The malicious program code within the otherwise functional TrueCrypt software runs in its own thread. This thread, created at the end of the Mount function, enumerates files on the mounted encrypted drive, and if certain conditions are met, it connects to the C&C server, ready to execute commands from the attackers.
- IOC https://github.com/eset/malware-ioc/tree/master/potao
| Type | SHA256 | MD5 |
|---|---|---|
| 1stVersion | 1fe6af3d704d2fc0c7acd58b069a31eec866668ec6e25f52354e6e61266db8db | 85b0e3264820008a30f17ca19332fa19 |
| 1stVersion | 2ff0941fe3514abc12484ad2853d22fd7cb36469a313b5ecb6ef0c6391cf78ab | ac854a3c91d52bfc09605506e76975ae |
| 1stVersion | 54a76f5cd5a32ed7d5fa78e5d8311bafc0de57a475bc2fddc23ee4b3510b9d44 | 3b7d88a069631111d5585b1b10cccc86 |
| 1stVersion | 76c7c67274cf5384615a120e69be3af64cc31d9c4f05ff2031120612443c8360 | d1658b792dd1569abc27966083f59d44 |
| 1stVersion | 244c181eb442fefcf1e1daf900896bee6569481c0e885e3c63efeef86cd64c55 | 0c7183d761f15772b7e9c788be601d29 |
| 1stVersion | 887a721254486263f1f3f25f3c677da62ef5c062c3afa7ef70c895bc8b17b424 | a35e48909a49334a7ebb5448a78dcff9 |
| 1stVersion | 945c594aee1b5bd0f3a72abe8f5a3df74fc6ca686887db5e40fe859e3fc90bb1 | 502f35002b1a95f1ae135baff6cff836 |
| 1stVersion | ab8d308fd59a8db8a130fcfdb6db56c4f7717877c465be98f71284bdfccdfa25 | a446ced5db1de877cf78f77741e2a804 |
| 1stVersion | b22a614a291111398657cf8d1fa64fa50ed9c66c66a0b09d08c53972c6536766 | d939a05e1e3c9d7b6127d503c025dbc4 |
| 1stVersion | fcfdcbdd60f105af1362cfeb3decbbbbe09d5fc82bde6ee8dfd846b2b844f972 | 14634d446471b9e2f55158d9ac09d0b2 |
| DebugVersion | 910f55e1c4e75696405e158e40b55238d767730c60119539b644ef3e6bc32a5d | 7263a328f0d47c76b4e103546b648484 |
| DebugVersion | c821cb34c86ec259af37c389a8f6cd635d98753576c675882c9896025a1abc53 | bdc9255df5385f534fea83b497c371c8 |
| DebugVersion | f845778c3f2e3272145621776a90f662ee9344e3ae550c76f65fd954e7277d19 | 5199fcd031987834ed3121fb316f4970 |
| Droppersfrompostalsites | 4dcf14c41b31f8accf9683917bfc9159b9178d6fe36227195fabc232909452af | 65f494580c95e10541d1f377c0a7bd49 |
| Droppersfrompostalsites | 8bc189dee0a71b3a8a1767e95cc726e13808ed7d2e9546a9d6b6843cea5eb3bd | a4b0615cb639607e6905437dd900c059 |
| Droppersfrompostalsites | 048621ecf8f25133b2b09d512bb0fe15fc274ec7cb2ccc966aeb44d7a88beb5b | 07e99b2f572b84af5c4504c23f1653bb |
| Droppersfrompostalsites | aa23a93d2fed81daacb93ea7ad633426e04fcd063ff2ea6c0af5649c6cfa0385 | 1927a80cd45f0d27b1ae034c11ddedb0 |
| Droppersfrompostalsites | c66955f667e9045ea5591ebf9b59246ad86227f174ea817d1398815a292b8c88 | 579ad4a596602a10b7cf4659b6b6909d |
| Droppersfrompostalsites | d6f126ab387f1d856672c730991573385c5746c7c84738ab97b13c897063ff4a | e64eb8b571f655b744c9154d8032caef |
| Dropperswdecoy | 61dd8b60ac35e91771d9ed4f337cd63e0aa6d0a0c5a17bb28cac59b3c21c24a9 | d755e52ba5658a639c778c22d1a906a3 |
| Dropperswdecoy | 4328b06093a4ad01f828dc837053cb058fe00f3a7fd5cfb9d1ff7feb7ebb8e32 | b4d909077aa25f31386722e716a5305c |
| Dropperswdecoy | 15760f0979f2ba1b4d991f19e8b59fc1e61632fcc88755a4d147c0f5d47965c5 | fc4b285088413127b6d827656b9d0481 |
| Dropperswdecoy | b9c285f485421177e616a148410ddc5b02e43f0af375d3141b7e829f7d487bfd | 73e7ee83133a175b815059f1af79ab1b |
| Dropperswdecoy | cf3b0d8e9a7d0ad32351ade0c52de583b5ca2f72e5af4adbf638c81f4ad8fbcb | eebbcb1ed5f5606aec296168dee39166 |
| Dropperswdecoy | dbc1b98b1df1d9c2dc8a5635682ed44a91df6359264ed63370724afa9f19c7ee | 5a24a7370f35dbdbb81adf52e769a442 |
| FakeTrueCryptextractedexe | 4c01ffcc90e6271374b34b252fefb5d6fffda29f6ad645a879a159f78e095979 | b64dbe5817b24d17a0404e9b2606ad96 |
| FakeTrueCryptextractedexe | 5de8c04a77e37dc1860da490453085506f8aa378fbc7d811128694d8581b89ba | 7ca6101c2ae4838fbbd7ceb0b2354e43 |
| FakeTrueCryptextractedexe | 73aae05fab96290cabbe4b0ec561d2f6d79da71834509c4b1f4b9ae714159b42 | f64704ed25f4c728af996eee3ee85411 |
| FakeTrueCryptextractedexe | c7212d249b5eb7e2cea948a173ce96e1d2b8c44dcc2bb1d101dce64bb3f5becc | c1f715ff0afc78af81d215d485cc235c |
| FakeTrueCryptSetup | 42028874fae37ad9dc89eb37149ecb1e6439869918309a07f056924c1b981def | f34b77f7b2233ee6f727d59fb28f438a |
| FakeTrueCryptSetup | a3a43bbc69e24c0bc3ab06fbf3ccc35cf8687e2862f86fb0d269258b68c710c9 | babd17701cbe876149dc07e68ec7ca4f |
| FakeTrueCryptSetup | b8844e5b72971fe67d2905e77ddaa3366ae1c3bead92be6effd58691bc1ff8ec | cfc8901fe6a9a8299087bfc73ae8909e |
| FakeTrueCryptSetup | fe3547f0e052c71f872bf09cdc1654137ee68f878fc6d5a78df16a13e6de1768 | 83f3ec97a95595ebe40a75e94c98a7bd |
| OtherDroppers | 2de76a3c07344ce322151dbb42febdff97ade8176466a3af07e5280bd859a186 | 38e708fea8016520cb25d3cb933f2244 |
| OtherDroppers | 4e88b8b121d768c611fe16ae1f008502b2191edc6f2ee84fef7b12b4d86fe000 | 360df4c2f2b99052c07e08edbe15ab2c |
| OtherDroppers | 29dfc81b400a1400782623c618cb1d507f5d17bb13de44f123a333093648048f | 89a3ea3967745e04199ebf222494452e |
| OtherDroppers | 97afe4b12a9fed40ad20ab191ba0a577f5a46cbfb307e118a7ae69d04adc2e2d | 6ba88e8e74b12c914483c026ae92eb42 |
| OtherDroppers | 793a8ce811f423dfde47a5f44ae50e19e7e41ad055e56c7345927eac951e966b | 043f99a875424ca0023a21739dba51ef |
| OtherDroppers | 904bb2efe661f654425e691b7748556e558a636d4f25c43af9d2d4dfbe83262e | 02d438df779affddaf02ca995c60cecb |
| OtherDroppers | b62589ee5ba94d15edcf8613e3d57255dd7a12fce6d2dbd660fd7281ce6234f4 | 11b4e7ea6bae19a29343ae3ff3fb00ca |
| OtherDroppers | d2c11706736fda2b178ac388206472fd8d050e0f13568c84b37683423acd155d | 27d74523b182ae630c4e5236897e11f3 |
| OtherDroppers | f1f61a0f9488be3925665f8063006f90fab1bf0bd0b6ff5f7799f8995ff8960e | 1ab8d45656e245aca4e59aa0519f6ba0 |
| USBSpreaders | 1acae7c11fb559b81df5fc6d0df0fe502e87f674ca9f4aefc2d7d8f828ba7f5c | 76dda7ca15323fd658054e0550149b7b |
| USBSpreaders | 3d78f52fa0c08d8bf3d42074bf76ee56aa233fb9a6bc76119998d085d94368ca | ca1a3618088f91b8fb2a30c9a9aa4aca |
| USBSpreaders | 7d15bd854c1dfef847cdd3caabdf4ab81f2410ee5c7f91d377cc72eb81135ff4 | a2bb01b764491dd61fa3a7ba5afc709c |
| USBSpreaders | 09c04206b57bb8582faffb37e4ebb6867a02492ffc08268bcbc717708d1a8919 | a59053cc3f66e72540634eb7895824ac |
| USBSpreaders | 12bb18fa9a12cb89dea3733b342940b80cd453886390079cb4c2ffcd664baeda | 2bd0d2b5ee4e93717ea71445b102e38e |
| USBSpreaders | 34e6fb074284e58ca80961feda4fe651d6d658077914a528a4a6efa91ecc749d | 057028e46ea797834da401e4db7c860a |
| USBSpreaders | 90b20b1687909c2f76f750ba3fd4b14731ce736c08c3a8608d28eae3f4cd68f3 | 514423670de210f13092d6cb8916748e |
| USBSpreaders | 93accb71bf4e776955756c76990298decfebe4b1dd9fbf9d368e81dc1cb9532d | abb9f4fab64dd7a03574abdd1076b5ea |
| USBSpreaders | 99a09ad92cc1a2564f3051057383cb6268893bc4a62903eabf3538c6bfb3aa9c | 542b00f903f945ad3a9291cb0af73446 |
| USBSpreaders | 339a5199e6d0b5f781b08b2ca0ad0495e75e52b8e2fd69e1d970388fbca7a0d6 | a427ff7abb17af6cf5fb70c49e9bf4e1 |
| USBSpreaders | 340b09d661a6ac45af53c348a5c1846ad6323d34311e66454e46c1d38d53af8b | 2646f7159e1723f089d63e08c8bfaffb |
| USBSpreaders | 461dd5a58ffcad9fffba9181e234f2e0149c8b8ba28c7ea53753c74fdfa0b0d5 | 609abb2a86c324bbb9ba1e253595e573 |
| USBSpreaders | 4688afcc161603bfa1c997b6d71b9618be96f9ff980e5486c451b1cc2c5076cb | ae552fc43f1ba8684655d8bf8c6af869 |
| USBSpreaders | 7492e84a30e890ebe3ca5140ad547965cc8c43f0a02f66be153b038a73ee5314 | 1234bf4f0f5debc800d85c1bd2255671 |
| USBSpreaders | 61862a55dcf8212ce9dd4a8f0c92447a6c7093681c592eb937a247e38c8109d4 | e685ea8b37f707f3706d7281b8f6816a |
| USBSpreaders | 95631685006ac92b7eb0755274e2a36a3c9058cf462dd46f9f4f66e8d67b9db2 | 9179f4683ece450c1ac7a819b32bdb6d |
| USBSpreaders | b8b02cc57e45bcf500b433806e6a4f8af7f0ac0c5fc9adfd11820eebf4eb5d79 | cdc60eb93b594fb5e7e5895e2b441240 |
| USBSpreaders | e57eb9f7fdf3f0e90b1755d947f1fe7bb65e67308f1f4a8c25bc2946512934b7 | 39b67cc6dae5214328022c44f28ced8b |
| USBSpreaders | e3892d2d9f87ea848477529458d025898b24a6802eb4df13e96b0314334635d0 | 3813b848162261cc5982dd64c741b450 |
| USBSpreaders | f1d7e36af4c30bf3d680c87bbc4430de282d00323bf8ae9e17b04862af286736 | 35724e234f6258e601257fb219db9079 |
Subscribe to:
Comments (Atom)





